Blast Radius
Overview Blast Radius Exercise
The Blast Radius function enables rapid localization of suspected hosts, and scopes the lateral movement boundary, also known as the blast radius, to prioritize potential targets/destinations for investigation. This functionality is crucial for understanding how an attacker could potentially move laterally within a network after gaining initial access. By identifying and analyzing the reachability and vulnerabilities of hosts within the blast radius, security teams can effectively prioritize remediation efforts, reduce the attack surface, and implement stronger access controls to mitigate the risk of lateral movement.
Estimated Completion Time
10 minutes
Attack Surface Mitigation with Blast Radius Overview
Blast Radius not only identifies the immediate network vicinity of a compromised host but also provides insights into how an attacker might exploit vulnerabilities to escalate privileges or access sensitive information. This understanding is pivotal for attack surface mitigation, as it allows for:
- Prioritization of Vulnerabilities: By highlighting critical vulnerabilities within the blast radius, organizations can prioritize patching and remediation efforts based on the potential impact and exploitability of these vulnerabilities.
- Enhanced Network Segmentation: Insights into the lateral movement pathways enable organizations to design and implement more effective network segmentation strategies, limiting the attacker's ability to move freely across the network.
- Improved Access Controls: Understanding the potential paths an attacker could take allows for the refinement of access controls, ensuring that users and systems have only the necessary permissions, thereby reducing the risk of privilege escalation.
- Proactive Threat Hunting: The detailed analysis provided by the Blast Radius function can guide proactive threat hunting activities, helping to identify and neutralize threats before they can exploit vulnerabilities within the network.
- Comprehensive Security Posture Assessment: By evaluating the blast radius in the context of an organization's network, security teams can gain a holistic view of their security posture, identifying areas of weakness and implementing strategies to strengthen overall network resilience.
In summary, the Blast Radius function is an essential tool for attack surface mitigation, offering a proactive approach to identifying, prioritizing, and addressing vulnerabilities that could be exploited in a lateral movement attack. By leveraging this functionality, organizations can enhance their security measures, reduce their attack surface, and better protect against sophisticated cyber threats.
Exercise 1: Accessing the Blast Radius Application
Objective: Learn how to access and use the Blast Radius application to identify potential targets within a network.
-
Navigate to Blast Radius: From the menu, select
Security-->Blast Radius. -
Enter Host Details: Input
nsx_vsw_host_001as the host, accept the defaults for Destination subnets and IP protocol exclusions, and click on the search button to execute the analysis.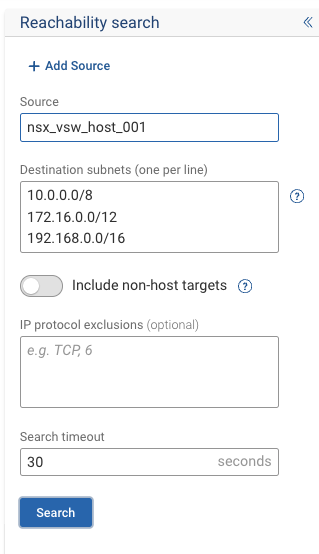
-
Below we can see the analysis that examines all reachability from the selected host to all other hosts in the network that are reachable.
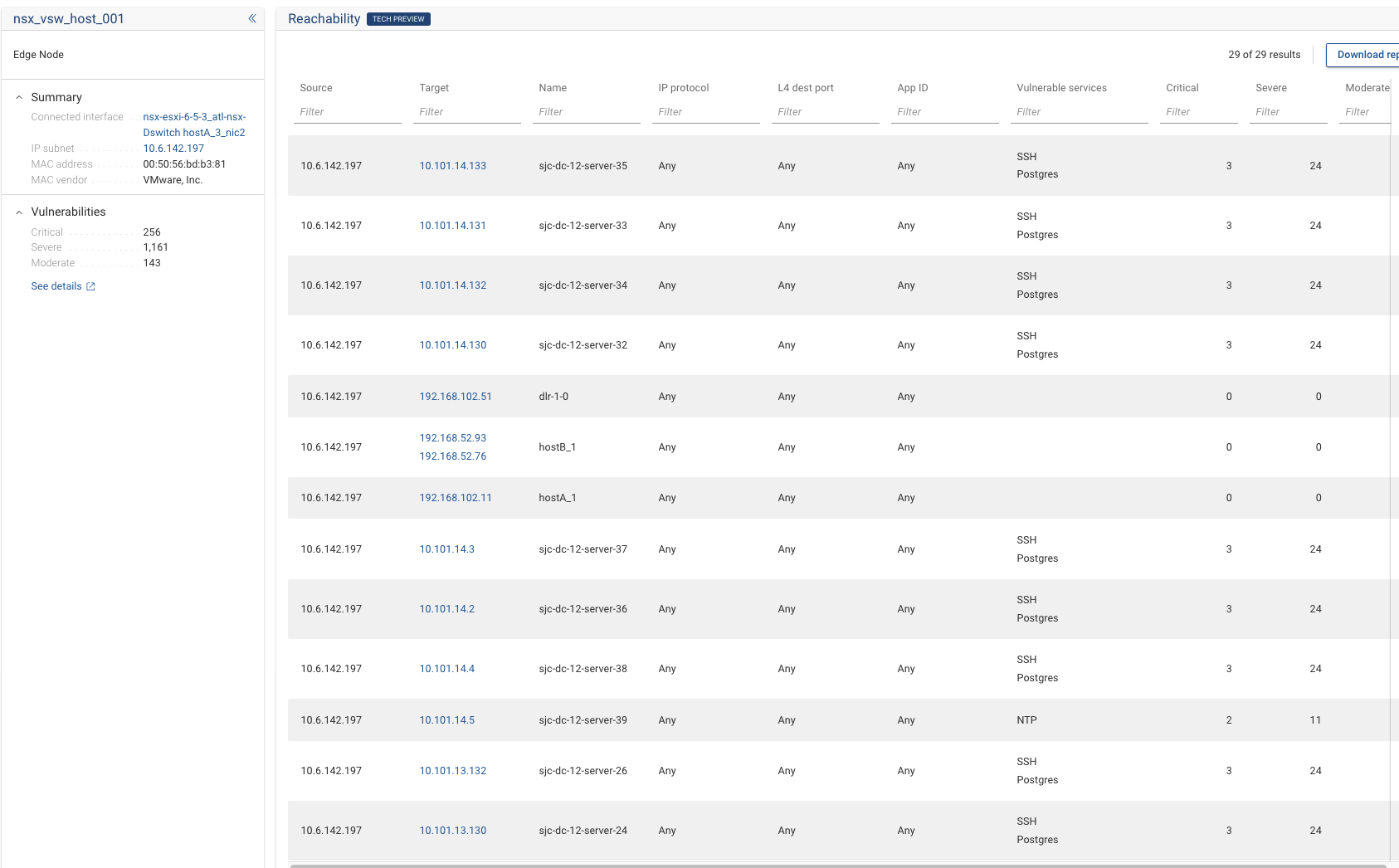
We can expand the search to not only hosts but also other devices if we select include non-host targets
Exercise 2: Analyzing the Results
Objective: Analyze the reachability and vulnerabilities of hosts within the blast radius to prioritize remediation efforts.
-
Review Reachability: Examine the analysis results to understand all reachable hosts from the selected host within the network.
-
Let's filter a specific hosts
10.117.161.6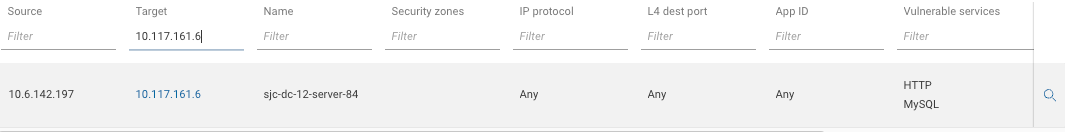
We can see we can reach this host over Any protocol and Any port.
We can also see that this host
10.117.161.6has been flagged with vulnerable servicesMySQLandHTTP. -
By clicking the magnifying glass
we can examine detailed path search.
We have resolved the address 10.117.161.6 into a hostname sjc-dc-12-server-84
-
Identify Vulnerabilities: Focus on hosts flagged with vulnerable services such as
mysqlandPostgreSQLand use the detailed path search to understand potential attack paths. -
Let's refine our search by inserting
mysqlinto the filters using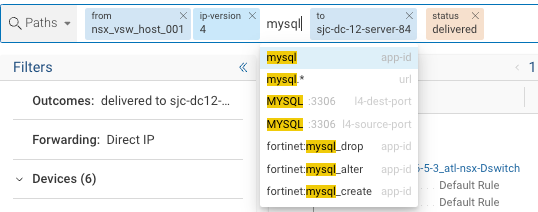 mysql app-id
mysql app-id
Insert the filter before the To
-
We now can clearly see that host
nsx_vsw_host_001can clearly connected tosjc-dc-12-server-84overmysqlwhich is a vulnerable service.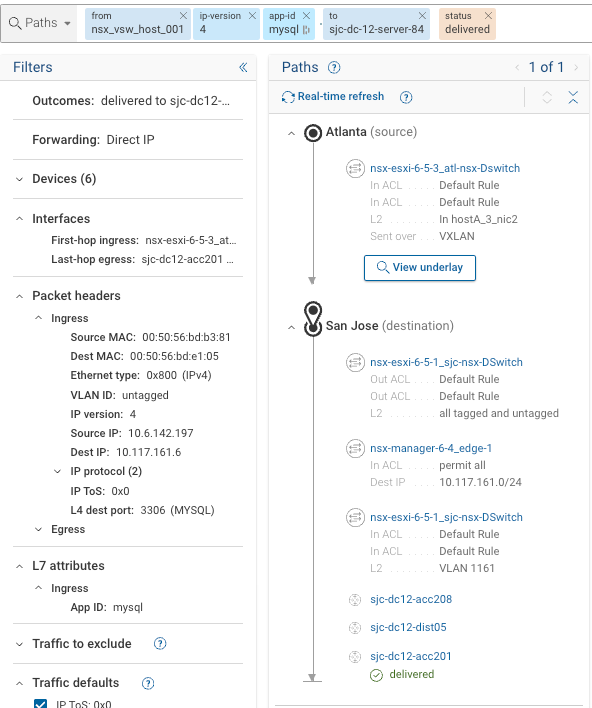
Key Insights
- Rapid Localization and Scope Identification: The Blast Radius function quickly identifies suspected hosts and their potential impact, aiding in prioritization for investigation and remediation.
- Prioritization of Remediation Efforts: Security teams can prioritize vulnerabilities within the blast radius for patching, based on their impact and exploitability.
- Enhanced Security Measures: Insights from the Blast Radius analysis help in enhancing network segmentation, refining access controls, and implementing stronger security measures to mitigate lateral movement risks.
- Proactive Threat Hunting: The function guides proactive threat hunting activities, aiming to neutralize threats before they exploit network vulnerabilities.
- Holistic Security Posture Assessment: Evaluating the blast radius within an organization's network offers a comprehensive view of the security posture, identifying weaknesses and guiding strategies to strengthen network resilience.
- Practical Application and Detailed Analysis: The exercises demonstrate accessing the Blast Radius application and analyzing results in detail, including refining searches based on specific criteria to better understand potential attacker pathways.
These insights highlight the importance of the Blast Radius function in cybersecurity, offering a proactive approach to identifying, prioritizing, and mitigating potential threats within a network.